Basic Policy
Cyberattacks in the digital space have become more sophisticated and prominent worldwide. Threats such as cyberattacks via ransomware, computer viruses, large-scale information leaks, and business email fraud are increasing.
i-PRO Corporation and its affiliated companies (hereinafter referred to as "the Company" or "We") have established an information security management system based on relevant information security regulations, and we routinely take security measures by constantly improving our information systems and employing multilayer protection.
In addition, we have obtained ISO 27001 certification to demonstrate our commitment to security.
Declaration of Information Security
We recognize the importance of protecting our customers’ personal information and other sensitive data. We will comply with laws, regulations, and technical standards to handle information assets accurately, safely, and appropriately according to their risk. We have implemented the following initiatives to earn the trust of our partners and customers.
- We strive to ensure the confidentiality, integrity, and availability of the information assets we hold.
- We will not disclose information unless there is a reasonable need to do so, such as a compulsory legal request.
- We strive to always maintain and improve information security by establishing an organization dedicated to improving information security for the purpose of protecting information assets, establishing rules for measures to ensure information security, providing education on information management, evaluating effectiveness, conducting audits, and making improvements.
- All officers and employees will take strict action, in accordance with prescribed procedures, against any action that compromises the confidentiality, integrity, or availability of information assets.
Organization
In our Information Security Policy, we outline how information is classified, stored, and protected. The policy also highlights our commitment to protecting sensitive data and complying with applicable data protection laws.
At i-PRO Corporation and its affiliated companies, the Information Security Office is the primary promoter and executor of information security.
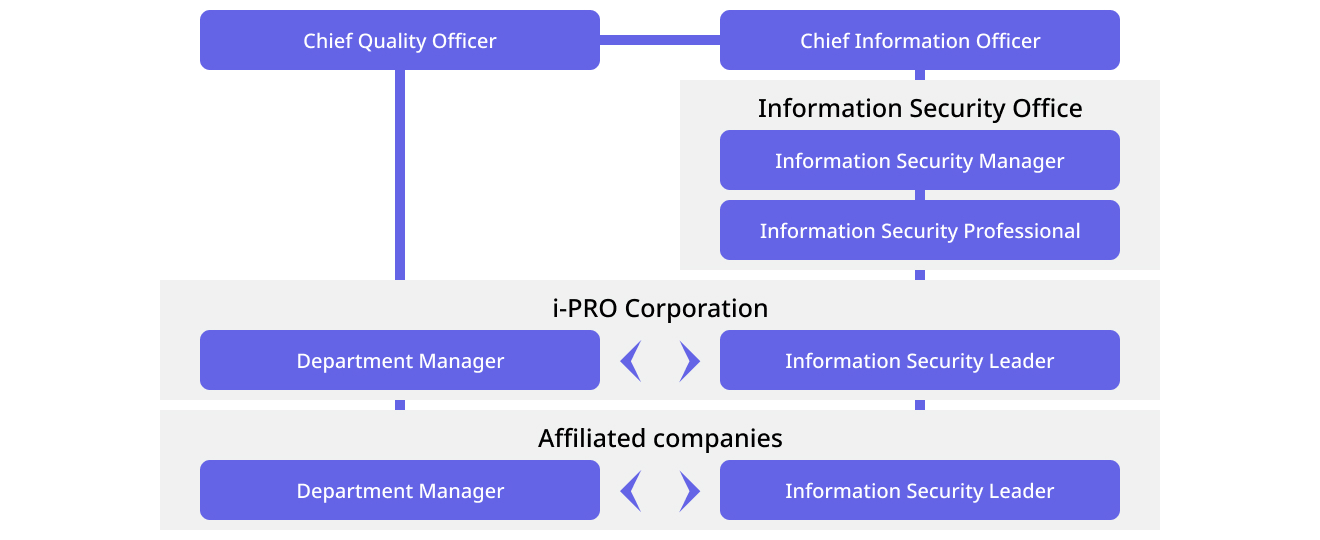
In our business, personal information is an essential part of the services we provide, and we consider it an important asset entrusted to us by our customers. In the unlikely event of an incident involving information security, such as the leakage of personal information, the incident is to be reported to the Information Security Office through the person in charge of the department manager where the incident occurred.
In the event of a serious incident, we will promptly set up a crisis response system and respond to the emergency in cooperation with relevant parties inside and outside the company.
<Main Initiatives>
Personal Information Protection
In recent years, successive laws and regulations concerning personal information and privacy have been enacted in Japan and overseas, and we have also developed our privacy policy and related internal rules to handle such information in compliance with the General Data Protection Regulation (GDPR) in Europe, the Cyber Security Law (CSL) and Personal Information Protection Law (PIPL) in China, the California Privacy Rights Act (CPRA) in the U.S., and the revised Act on the Protection of Personal Information (APPI) in Japan.
We are also strengthening our efforts to properly handle the personal information of our customers, stakeholders, business partners, and employees by providing education on these laws and regulations as well as related internal rules.
Cybersecurity Measures
We deploy multilayer protection cybersecurity strategy and monitor our networks 24 hours a day, 365 days a year, to ensure that we can respond quickly in the event of an incident.
In addition, since early warnings of cyberattacks are critical for cybersecurity, we use collaborative tools to discover industry and cyberattack trends to take preventive measures when necessary.
We understand that even the best-prepared organizations may fall victim to cyber incidents, so we are introducing a zero-trust approach to conventional security measures. To improve security among supply chains in a society connected to all types of businesses and industries, we will strengthen cooperation with relevant ministries and agencies, economic organizations (e.g., the Japan Business Federation [Keidanren]), and private security organizations (e.g., the Information Sharing and Analysis Center [ISAC]).
Development of Professional Personnel
In addition, we are building a system to minimize the impact of problems by promptly establishing an initial response system and taking countermeasures in cooperation with each department in case a problem occurs.
Education
To ensure that all employees understand the importance of information security, including the protection of personal information and the threat of cyberattacks, and take actions to protect information assets, we regularly provide e-learning programs for all employees to impart knowledge, including the latest case studies.
Risk Assessment
We regularly conduct risk assessments of information security at our domestic and overseas offices to inspect the management status of information assets from a third-party perspective, identify any issues, and make improvements.